Azure Sentinel brings together all your logs from all sources, via the Log Analytics workspace, to correlate and search for threats. Sentinel uses connectors to integrate with Microsoft 365, Active Directory, and many third-party vendors such as Cisco, Carbon Black, and F5 networks. By combining information from many different sources, an attack can be tracked and investigated across the entire IT stack.
Azure Sentinel is priced by the amount of log data ingested, and so you can choose which log sources to ingest. Known as a data connector, you configure Sentinel to only ingest the log sources you are interested in, although of course the more you connect, the greater visibility you have.
Once connected, Azure offers a series of analytical templates from which you can easily create rules, or you can use them as a starting point and create your own. Rules are analytical queries that search for specific attack types, which you can then use to generate an alert from.
The following screenshot shows an example of templates you can choose from for a given data connector:
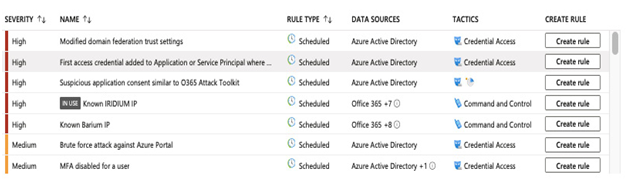
Figure 15.16 – Creating rules from pre-defined templates
As well as sending alerts when rules are triggered, you can also create automation runbooks to perform automated actions. These can be as simple as integrating with your helpdesk solution to generate tickets, or even responding directly to the threat by performing a specific action. For example, if a source is detected as performing a SQL injection attack, you can create a playbook that would automatically blacklist that IP address on your Azure Firewall.
The Sentinel overview page shows all your ingested events, alerts, and incidents, as you can see in the following example:
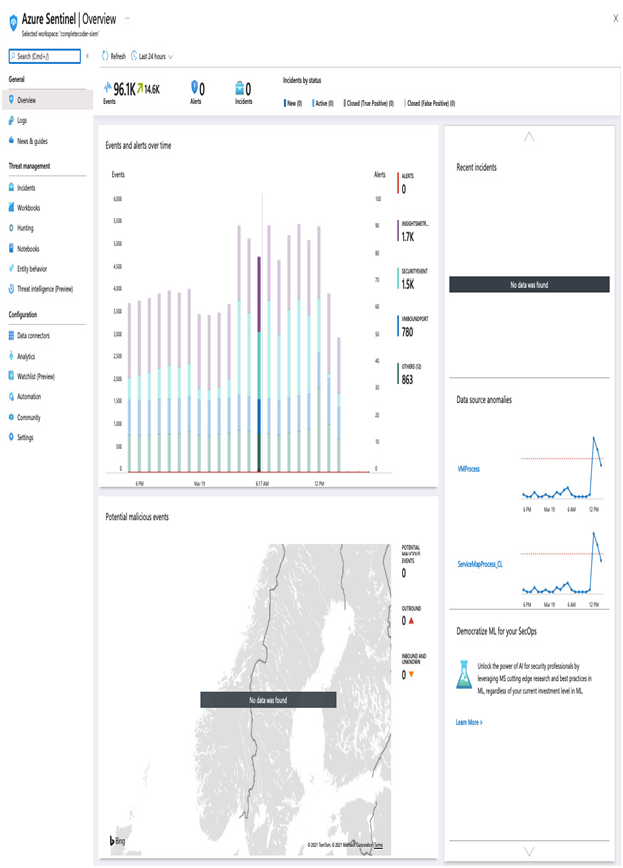
Figure 15.17 – Azure Sentinel overview page
When threats are detected, Sentinel provides you with investigative tools that help to trace and hunt down the attack. You can select an incident from the Incidents view and locate the root cause by seeing what happened before and after the incident, where it occurred, links, and related information.
The Hunting tool allows security professionals to proactively investigate your Azure solutions for potential or in-progress attacks before they happen. Sentinel provides a series of starting queries to help with this, or you can build your own.
Sentinel also provides a series of Jupyter notebooks so that you can use machine learning, using an Azure Machine Learning workspace to further enhance your investigations.
Threat detection and remediation are specialist areas and often involve dedicated security teams or a Security Operations Center (SOC). As an architect, it is your responsibility to ensure the right tools are provided for your organization’s needs.
From a monitoring and alerting perspective, you therefore need to understand how Log Analytics, Security Center, Defender, and Sentinel fit together.
The end-to-end process is to log and collect data, identify activities, pro-actively protect, detect anomalies, respond to threats, and then recover. The following diagram shows how each of the available tools works together to achieve this:
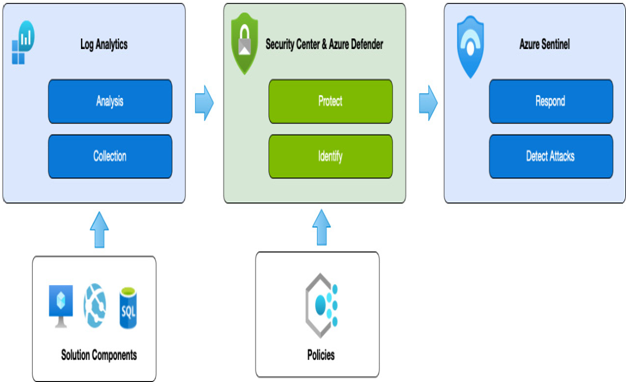
Figure 15.18 – Security ecosystem
The use of security and monitoring tooling is a big subject and detailed knowledge is needed for the AZ-500 Microsoft Azure Security Technologies exam. For the AZ-304 exam, you need to know how the different solutions fit together and what each achieves.
In the final section of this chapter, we will cover another built-in set of tools that help you keep an eye on costs and efficiency.

Leave a Reply